As I diligently pursue my ongoing certification to become an ethical hacker, certified by the EC Council, I frequently encounter discussions about the potential threats lurking on publicly accessible Wi-Fi hotspots. This topic has become a recurring concern during my studies.
Recently, while enjoying a vacation at a modern and well-equipped hotel in Turkey, I decided to put my knowledge to the test. I wanted to determine whether the unsettling tales I’ve heard during my lectures were indeed grounded in reality or merely exaggerated for the sake of the author’s book sales, possibly verging on science fiction.
With my background in ethical hacking, I embarked on a mission to investigate the security vulnerabilities of the hotel’s public WiFi network. This excursion served as a practical experiment, aiming to validate the warnings I had encountered in my certification training. In doing so, I hoped to shed light on the true extent of the risks associated with using public hot spots and whether they mirrored the ominous scenarios presented in my coursework.

So, I’m now sitting here near the hotel lobby bar with my Kali Linux and a rather conspicuous external antenna, commencing my experiment. It doesn’t seem to bother anyone here initially, or I don’t appear to draw much attention, as the waitstaff and the guests are more focused on themselves or their drinks.
Captive Portal
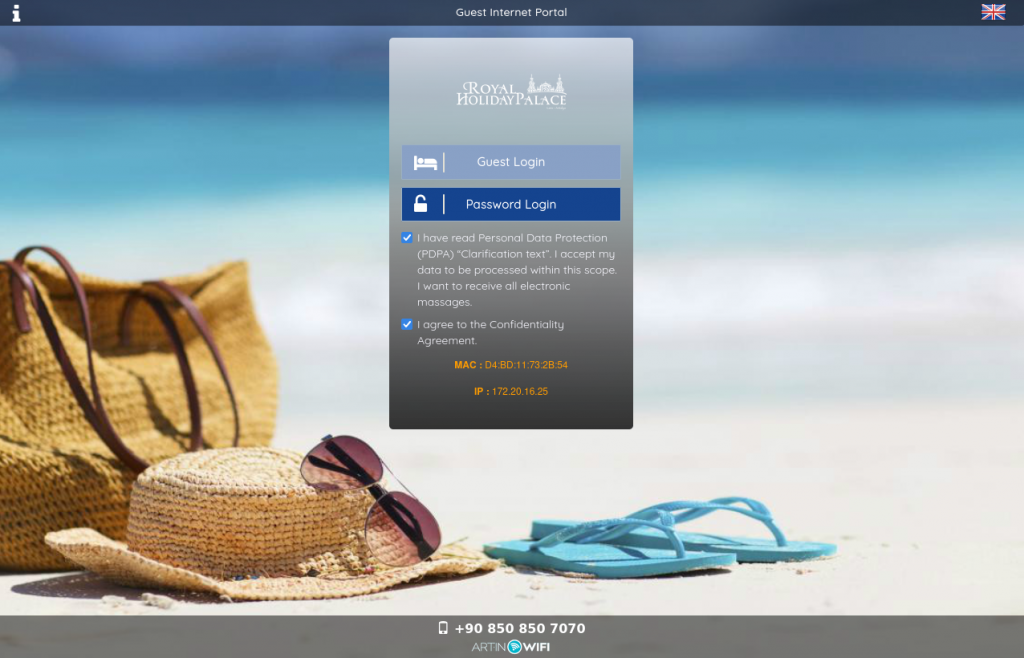
When connecting to the hotel’s Wi-Fi for the first time, you’ll be prompted to register as a guest. During this process, you’ll be required to provide your date of birth, email address, and room number. Afterward, access to the network and, consequently, the internet, will be granted without any further obstacles.
The website to which you are automatically redirected is called a Captive Portal, and it is more or less a standard procedure in all public WiFi’s.
However, since I want to remain anonymous, the last thing I want to do is to register myself.
The following steps are not intended to be replicated, and if attempted, should be done solely for educational purposes. Unauthorized or unethical access to networks and systems is against the law and goes against ethical principles. It is essential to respect all applicable laws, regulations, and ethical guidelines when working with computer systems, networks, and online resources. This information is provided for educational awareness and should not be used for any malicious or illegal activities. Always act responsibly and within the boundaries of the law and ethical standards when engaging in any form of network or system testing or exploration.
In general Captive Portals work like this
- Devices provide their unique MAC address.
- The MAC address is compared to a whitelist.
- Whitelisted devices gain network access without redirection.
So changing the MAC address either with windows or linux is very simple. The approach will be to spoof a MAC address from someone who has already completed the registration process.
Step 1 – Take a look around to see whats going on
sudo su -
ifconfig wlan0 down && iwconfig wlan0 mode Monitor && ifconfig wlan0 upThis sets the wlan0 adapter into monitor mode which allows not only to see all of the packets of a certain network but also any packet received by any network in range. For the sake of this demo I made a scan within the 2.4 GHz range:
airodump-ng wlan0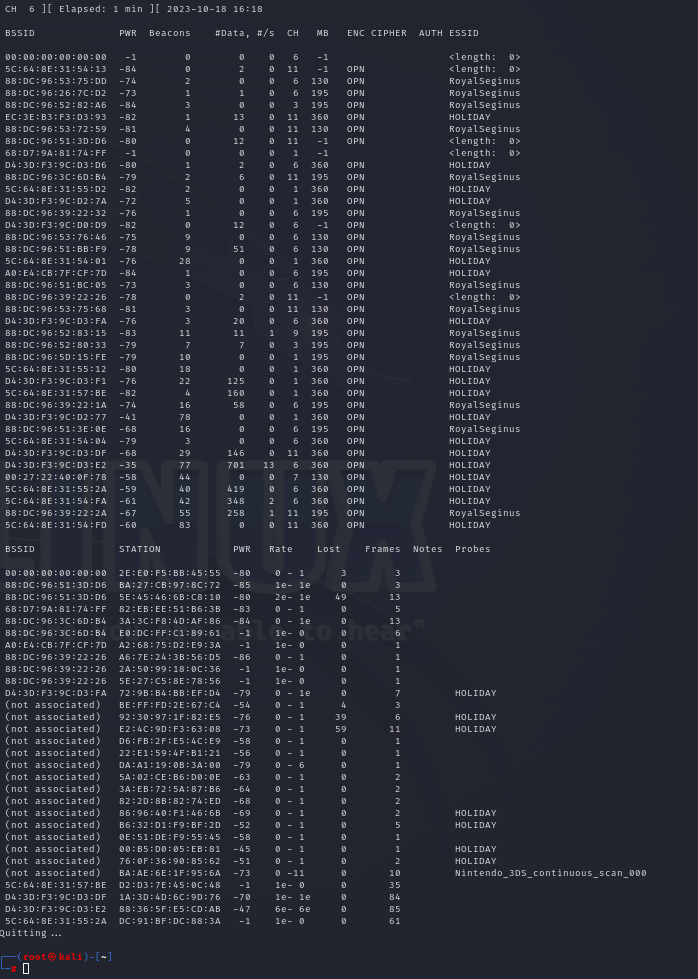
As can be observed, there is a lot of activity on the network. The upper section lists all the received access points, while the lower section lists the connected stations, such as smartphones, tablets, or laptops.
Step 2 – Impersonate a registered station by changing the MAC address of my laptop
The approach is now quite straightforward: select a MAC address from a station that has already successfully connected, change your own MAC address to match it, and then connect to the network.
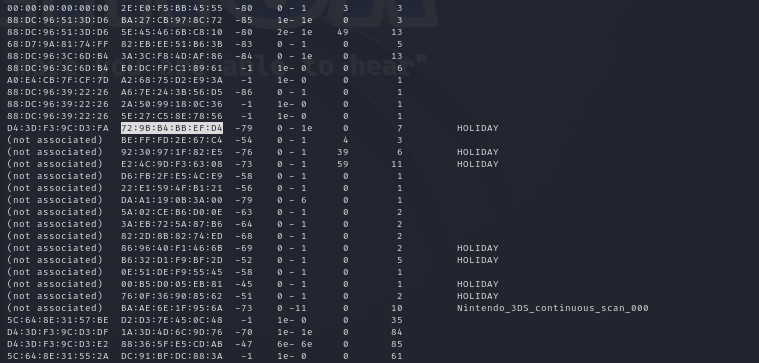
macchanger -m 72:9B:B4:BB:EF:D4 wlan0So, that’s pretty much it. Now, I should be able to connect to the network without having to register beforehand.
Step 3 – Connect to the internet
Now, one could naturally say – okay, but others have already figured this out, and there are numerous YouTube videos that describe exactly what was explained. Furthermore, one might ask, what’s the issue? If you haven’t registered, then you simply haven’t registered.
It is indeed correct that this whitelisting and how to bypass it is relatively common knowledge. However, what is seldom mentioned in almost any YouTube video is the potential risks it poses for other registered network participants, and it’s these risks that I want to outline here.
As described earlier, this form of compromise is referred to as impersonation, which involves the illicit impersonation of another identity in various operations.
But why do you need to register in the first place?
To get registered you have to provide some information as mentioned before. In sum each time you utilize the Hotel WiFi you are identified uniquely by those information together with your stations MAC address e.g. your smartphone.
Have you noticed the „Personal Data Protection Clarification Text“ alongside with the „Confidentiality Agreement“ you have to accept in order to get successfully registered?

So, I would get an uneasy feeling at the thought that while I’m enjoying my cocktail by the pool, someone might be illicitly gaining access to the hotel’s Wi-Fi using my MAC address and breaking cybersecurity laws in my name. What makes me even more uncomfortable is the idea of a possible burden of proof reversal, where I would have to demonstrate that it wasn’t me. This can happen anytime one joins a public Wi-Fi network where registration is only required through a captive portal, and a simple MAC address whitelist is used for authorization.
This situation highlights the growing threat of identity theft and cybercrime in public Wi-Fi networks. The apparent security flaw in using MAC addresses for authorization poses significant risks to privacy and the legal responsibility of users.
It’s important to understand that MAC addresses can be easily forged or cloned, allowing an attacker to infiltrate a network and carry out illegal activities that can then be attributed to the original owner of the MAC address. This can range from minor violations of network policies to more serious offenses that can have substantial legal consequences.
The possibility of burden of proof reversal, where the user has to prove their innocence, presents a particular challenge. It can be difficult to demonstrate that you’re not responsible for actions taken under your MAC address. This can lead to considerable stress and legal difficulties.
To protect against such risks, it’s advisable to take some precautions. Users should ensure they only use trusted Wi-Fi networks, especially in public areas. Using Virtual Private Networks (VPNs) can also help enhance security and privacy, as they encrypt communication and make it more challenging to identify users solely based on MAC addresses.
Ultimately, the notion of someone clandestinely gaining access to Wi-Fi using your MAC address underscores the importance of being aware of the risks and taking appropriate measures to safeguard your identity and legal integrity. Cybersecurity shouldn’t exist solely in theory but should also be practiced to prevent potentially harmful scenarios like these.