Disclaimer: This text is provided solely for educational purposes. The steps described here should not be imitated or implemented in practice. Any activities that violate applicable laws, regulations, or ethical standards are strictly prohibited. All steps outlined below have been reversed upon completion of the experiment to ensure that no inappropriate use or harm occurred. It is important to adhere to the laws and regulations of your country and to follow ethical principles when engaging on the internet or conducting technical experiments. Abuse or illegal activities are not endorsed and may result in serious legal consequences.
The DarkNet: A Paradise for Shopping and Business Ventures
The DarkNet, that mysterious corner of the internet where the words „legitimacy“ and „trust“ are defined a tad differently than in the rest of the world. It might not be the first thing that comes to mind when you think of shopping, but believe it or not, the DarkNet is a true shopping paradise.
Sure, the DarkNet has its reputation, and it’s not exactly pristine. But that’s precisely what makes it so thrilling! If you’re in search of things that Amazon, eBay, or AliExpress don’t have in their portfolios, then the DarkNet is the place to be. Whether it’s drugs, counterfeit money, stolen data, weapons, or just contract killers you’re after – everyone’s catered to here.
But wait, I almost forgot to tell you my own story. Recently, I decided to dive into the DarkNet to promote my new business, CypherWise.info.

Sure, there are black sheep everywhere, even in the Darknet. But let me be honest, the Darknet is like a secret wonderland for creative minds who think outside the box. A few black sheep can’t deter me from pursuing my business idea there. Maybe those were just the exceptions that prove the rule. So, off I go into the Darknet, where innovation thrives in the shadows! 🌑💡 Now, I’m left wondering how I can implement my business idea using a hidden service?!
What is a hidden service?
A Hidden Service in the Darknet is a type of website or online service accessible through the Tor network. Unlike regular websites, where the server’s address is publicly known, a Hidden Service’s address remains secret, preserving anonymity for both the operator and users. This allows for the offering and accessing of content and services in the Darknet without revealing one’s identity. Hidden Services are often used for legitimate purposes like anonymous forums, online marketplaces, and communication in authoritarian regimes, but they can also be misused for illegal activities.
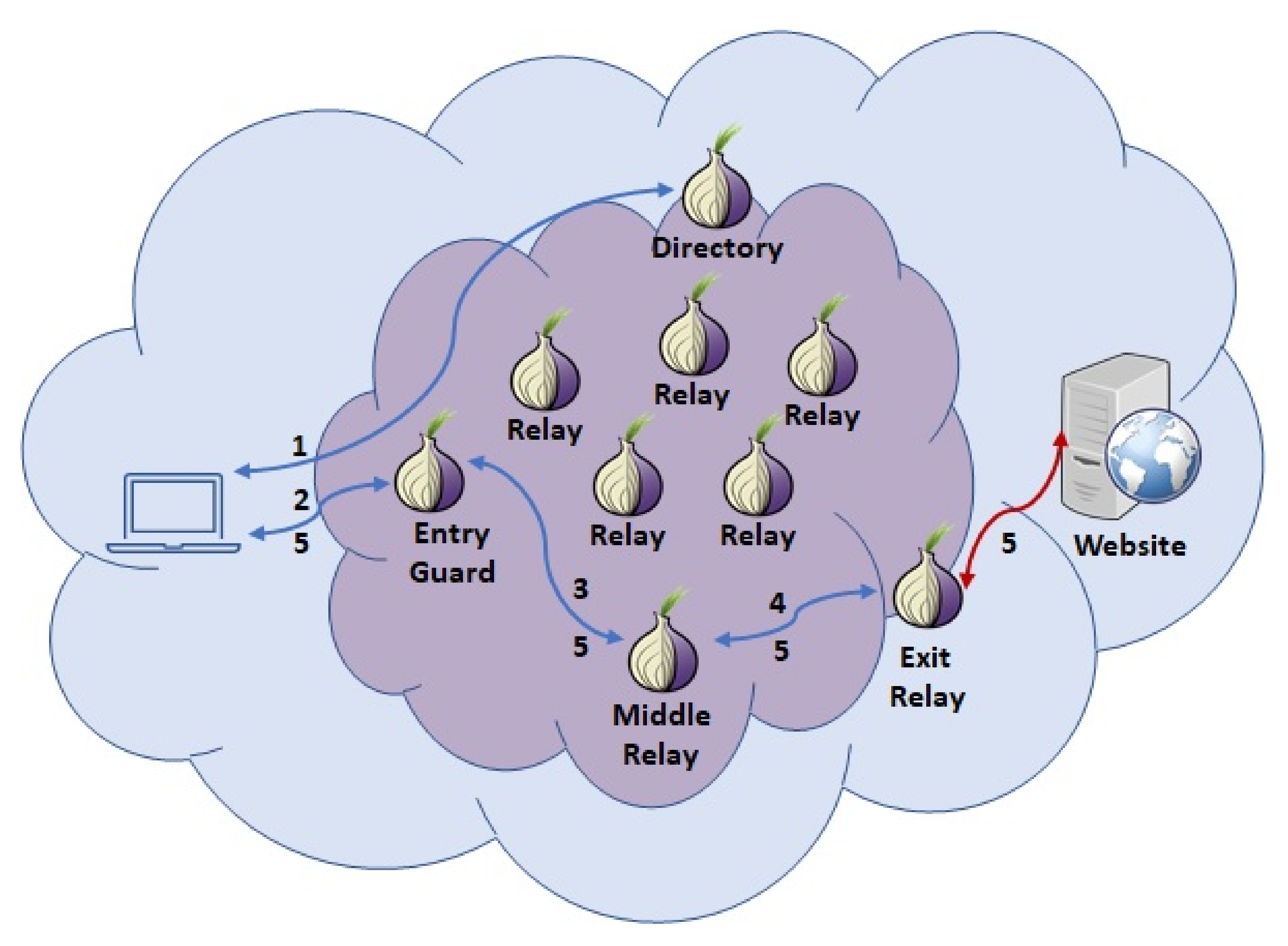
Setting up your own Hidden Service on the Darknet can be surprisingly straightforward, requiring just a few key components and some basic configuration. With a Raspberry Pi, the Tor service, Nginx, and your own website, you can create a platform accessible through the Tor network while maintaining anonymity.
So let’s do it!
First and foremost, you’ll need a Raspberry Pi, a compact and affordable computer that’s perfect for hosting your Hidden Service. Ensure it’s running a secure operating system, such as Raspbian.

Next, install the Tor service on your Raspberry Pi. Tor is essential for anonymizing both your server and users, making it an ideal choice for creating Hidden Services.
sudo apt update
sudo apt install tor -yNow, set up the Nginx web server on your Raspberry Pi. Nginx is known for its speed and efficiency, making it a solid choice for serving web content.
sudo apt install nginx -yWith your web server in place, it’s time to create your website or web application. This can be anything from a personal blog to an online forum or a private file-sharing service. Just ensure your content adheres to legal and ethical standards.
Well, here I am, faced with the task of creating my own website for the Darknet. But honestly, after all the work I’ve put into my current website, I’m not really in the mood for more coding. I mean, I’ve already spent enough time trying to make the „About Me“ section not sound like a bad self-help book!
And then I think to myself, the Darknet is kind of like the Wild West of the internet, right? There are probably no rules, or at least none that anyone really cares about. I could probably clone other websites without anyone batting an eye. And, honestly, would anyone even notice? After all, there’s no such thing as TLS server certificates for secure authentication in the Darknet, is there?
Let’s clone another ones hidden service
Cloning a simple website is quite an easy task with HTTrack. HTTrack is a free and open-source website mirroring tool that allows users to download and create a local copy of a website for offline browsing. It’s a useful tool for various purposes, including website backups, research, or accessing web content offline.
HTTrack can either be used on the command line or with an additional gui. I will use HTTrack together with torsocks, to not try to connect to a certain website on the Clearnet but on the DarkNet and the only way to achieve this, is to pass through the HTTrack command with SOCKS5 by utilizing torsocks.
sudo apt install torsocks -y
sudo apt install httrack -yNow, it’s just a matter of finding a beautiful website that could meet my requirements.
Here we go: A nice looking site which claims to offer stolen credit cards. I think it might fit for my purposes having my business represented quite accurately after a few ajustments.
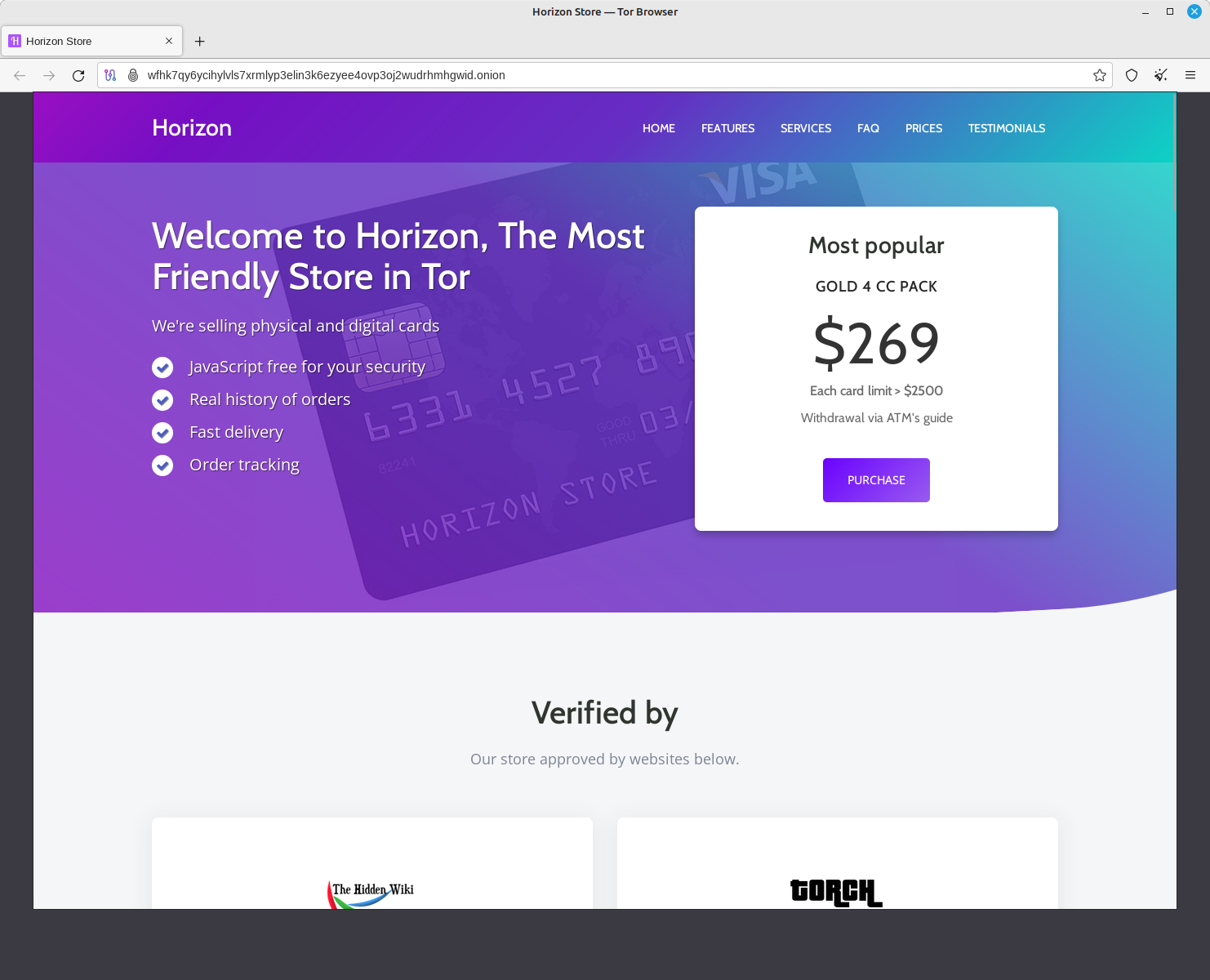
So let’s clone and store it locally in my nginx root folder
cd ~
torsocks httrack http://wfhk7qy6ycihylvls7xrmlyp3elin3k6ezyee4ovp3oj2wudrhmhgwid.onion
cd wfhk7qy6ycihylvls7xrmlyp3elin3k6ezyee4ovp3oj2wudrhmhgwid.onion/
sudo mkdir /var/www/cypherwise && sudo cp -r * /var/www/cypherwise
sudo chown -R www-data:www-data cypherwise/
cd /var/www/cypherwise
ll
drwxr-xr-x 2 www-data www-data 4096 Sep 24 17:47 css
drwxr-xr-x 2 www-data www-data 4096 Sep 24 17:47 img
-rw-r--r-- 1 www-data www-data 31025 Sep 24 17:49 index.html
-rw-r--r-- 1 www-data www-data 969 Sep 24 17:47 torchlogo.png
-rw-r--r-- 1 www-data www-data 6815 Sep 24 17:47 wiki.pngTo see if it’s really as delightfully simple as that, I will first just change the name from Horizon to Cypherwise, as well as the slogan, because I am not a trader but an advisor.
Some nginx configuration:
sudo nano /etc/nginx/sites-available/defaulterver {
listen 127.0.0.1:11111 default_server;
root /var/www/cypherwise;
index index.html index.htm index.nginx-debian.html;
server_name _;
location / {
# First attempt to serve request as file, then
# as directory, then fall back to displaying a 404.
try_files $uri $uri/ =404;
}
Some tor configurations:
sudo nano /etc/tor/torrcHiddenServiceDir /var/lib/tor/cypherwise/
HiddenServicePort 80 127.0.0.1:11111Setting nginx.service and tor.service to start on boot up:
sudo systemctl enable tor.service nginx.service
Getting my own onion-address:
sudo cat /var/lib/tor/cypherwise/hostname
sejfadyjlm4isj3we4ymedx5y6qu5r7lcds5fgybgwsgtwovjf62xwid.onionAnd finally:
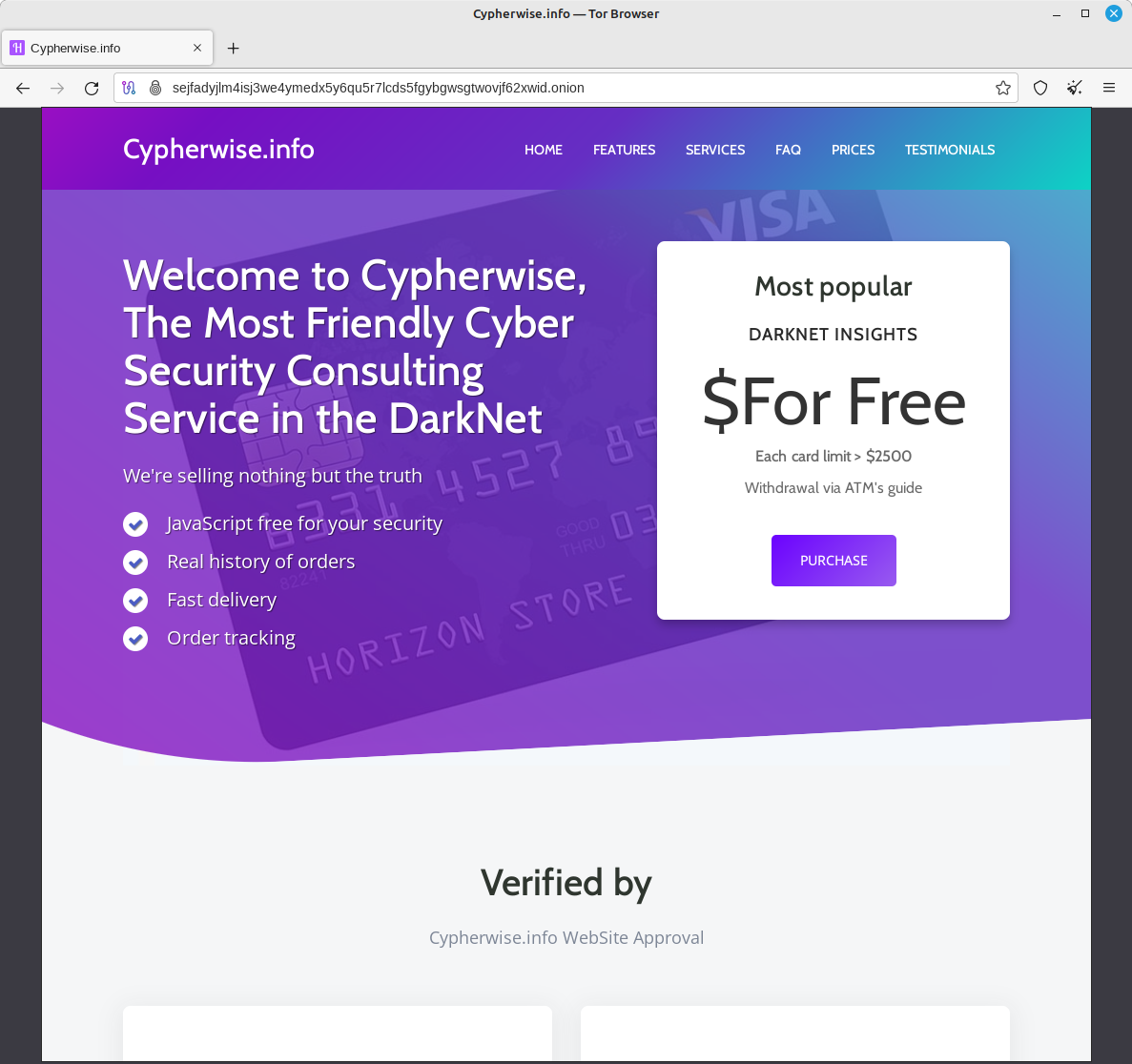
Great!!!
One can now see how easy it is to replicate a website. All that would be left is fine-tuning – such as search engine optimization, adding the link to a list of trusted and verified sites, and even directly registering with search engines.
However, let’s make it clear that these steps are intentionally not taken. The reason being is simple: it was important to demonstrate what is theoretically possible to make us aware of what we should protect ourselves from whenever possible.
Copying websites and attempting to pass them off as our own is not only unethical but can also have legal consequences. DarkNet integrity and respect for intellectual property are crucial. We should always strive to use the DarkNet / Internet in a manner that is ethical and compliant with the law, respecting the privacy and rights of others.
By the way: You think scamming is just a matter of DarkNet?
In a world where digitalization advances relentlessly, scammers are omnipresent. The darknet is merely one of numerous arenas where criminal activities unfold. Indeed, scams have proliferated rapidly in social media in recent years, assuming novel and creative forms time and again.
One of these burgeoning fraudulent methods involves the deliberate addition of fake members to Telegram channels, X followers, or even fake reviews in online commerce. This is often done to create the impression of authenticity and popularity, whether it’s for political purposes, product marketing, or simply to enhance one’s social standing.
How I Became an Influencer on Social Media Overnight:
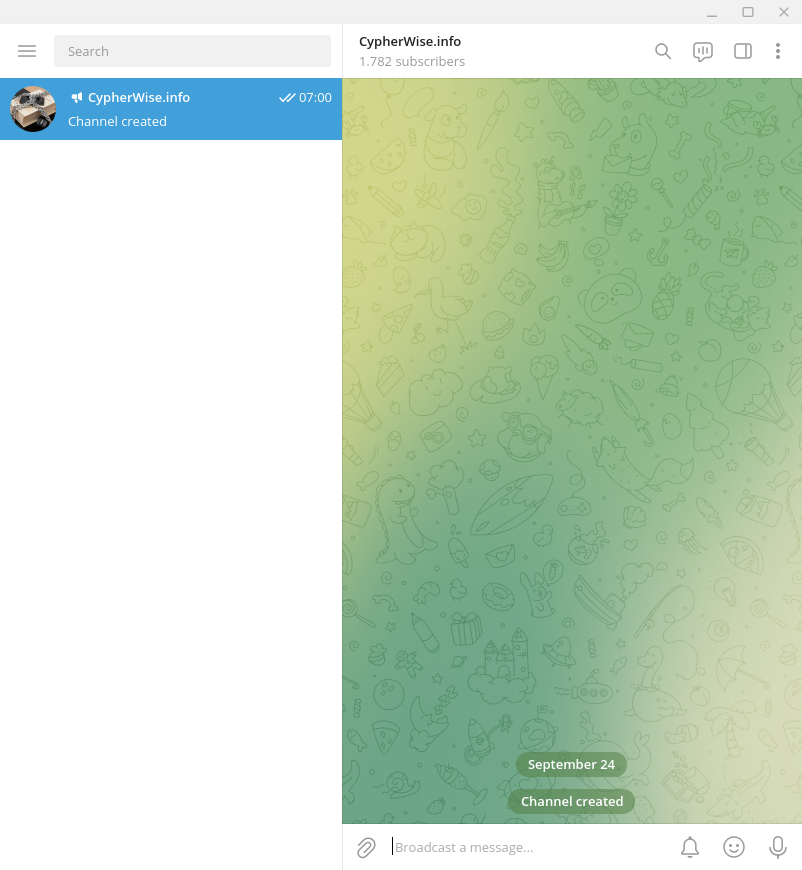
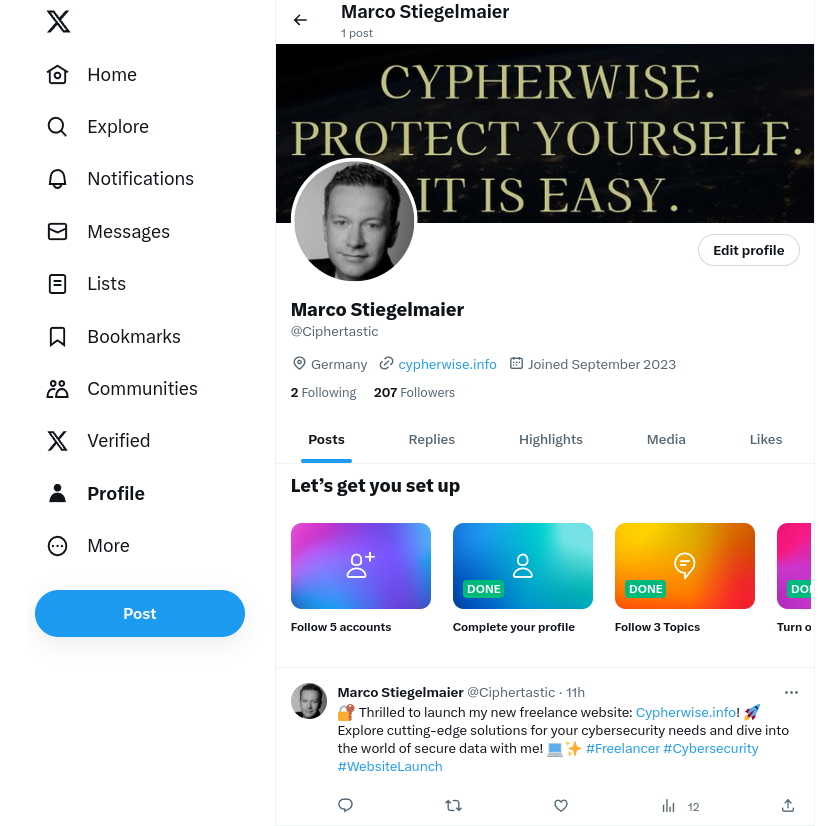
More than 1700 subscribers on my telegram channel without posting anything and more than 200 X-followers for just one ridiculous post?!
The solution:
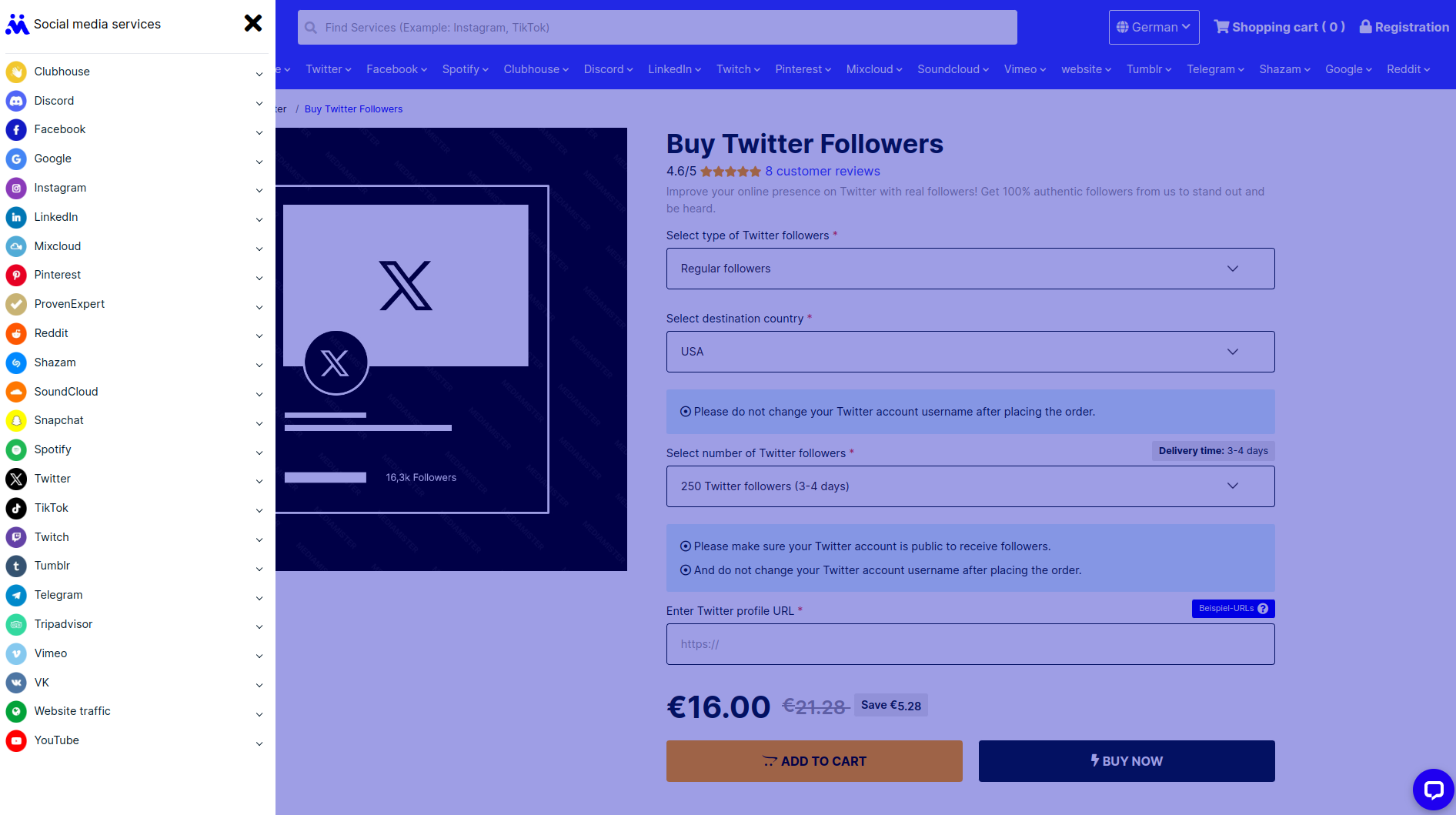
I did so with a fake Onionmail-Account together with some Bitcoin-Monero-Monero-Bitcoin money and here we go.
As a conclusion, I would like to emphasize that we are surrounded by fraud. Fraud has become so prevalent in all aspects of life, especially in the digital realm, that it can be challenging to distinguish between deception and truth. In this digital age, it’s more crucial than ever to exercise vigilance, critical thinking, and ethical conduct. Let us strive to protect our online communities and uphold the values of honesty and integrity in all our endeavors.
Marco Stiegelmaier